An interesting talk by the Head of Daimler Benz -- a bit mind blowing to say the least! He predicted an interesting concept of what could lay ahead. In a recent interview, the Head of Daimler Benz (Mercedes Benz) said their competitors are no longer other car companies, but Tesla (obviously), and now, Google, Apple, Amazon 'et al' are…… Software will disrupt most traditional industries in the next 5-10 years.. Uber is just a software tool, they don't own any cars, and are now the biggest taxi company in the world. Airbnb is now the biggest hotel company in the world, although they don't own any properties. Artificial Intelligence: Computers become exponentially better in understanding the world. This year, a computer beat the best Go player in the world, 10 years earlier than expected. In the U. S., young lawyers already can't get jobs. Because of IBM Watson, you can get legal advice (so far for more or less basic stuff) within seconds, with 90% accuracy compared with 70% accuracy when done by humans. So, if you study law, stop immediately. There will be 90% less lawyers in the future, only specialists will remain. Watson already helps nurses diagnosing cancer, 4 times more accurate than human nurses. Facebook now has a pattern recognition software that can recognize faces better than humans. In 2030, computers will become more intelligent than humans. Autonomous cars: In 2018 the first self-driving cars will appear for the public. Around 2020, the complete industry will start to be disrupted. You don't want to own a car anymore.. You will call a car with your phone, it will show up at your location and drive you to your destination. You will not need to park it, you only pay for the driven distance and you can be productive while driving. Our kids will never get a driver's license and will never own a car. It will change the cities, because we will need 90-95% less cars for that. We can transform former parking spaces into parks. 1.2 million people die each year in car accidents worldwide.. We now have one accident every 60,000 miles (100,000 km), with autonomous driving that will drop to one accident in 6 million miles (10 million km). That will save a million lives each year. Most car companies will probably go bankrupt. Traditional car companies will try the traditional approach and try to build a better car, while tech companies (Tesla, Apple, Google) will take the revolutionary approach and build a computer on wheels. Many engineers from Volkswagen and Audi are completely terrified of Tesla. Auto Insurance companies will have massive trouble because without accidents, car insurance will become much cheaper. Their car insurance business model will slowly disappear. Real estate will change. Because if you can work while you commute, people will move further away to live in a more beautiful neighborhood. Electric cars will become mainstream about 2020. Cities will be less noisy because all new cars will run on electricity. Electricity will become incredibly cheap and clean: Solar production has been on an exponential curve for 30 years, and now you can now see the burgeoning impact. Last year, more solar energy was installed worldwide than fossil. Energy companies are desperately trying to limit access to the grid to prevent competition from home solar installations, but that can't last. Technology will take care of that strategy. With cheap electricity comes cheap and abundant water. Desalination of salt water now only needs 2kwh per cubic meter (@ 0.25 cents). We don't have scarce water in most places, we only have scarce drinking water.. Imagine what will be possible if anyone can have as much clean water as he wants, for nearly no cost. Health innovations: The Tricorder X price will be announced this year. There are companies who will build a medical device (called the "Tricorder" from Star Trek) that works with your phone, which takes your retina scan, your blood sample, and you can breath into it. It then analyses 54 biomarkers that will identify nearly any disease. It will be cheap, so in a few years everyone on this planet will have access to world class medical analysis, nearly for free. Goodbye, medical establishment. 3D printing: The price of the cheapest 3D printer came down from $18,000 to $400 within 10 years. In the same time, it became 100 times faster. All major shoe companies have already started 3D printing shoes. Some common spare airplane parts are already 3D printed in remote airports. The space station now has a printer that eliminates the need for the large amount of spare parts they used to keep in the past. At the end of this year, new smart phones will have 3D scanning possibilities. You can then 3D scan your feet and print your perfect shoes at home. In China, they already 3D printed and built a complete 6-storey office building. By 2027, 10% of everything that's being produced will be 3D printed. Business opportunities: If you think of a niche you want to go in, ask yourself: "In the future, do you think we will have that?", and if the answer is yes, how can you make that happen sooner? If it doesn't work with your phone, forget the idea. And any idea designed for success in the 20th century is doomed to failure in the 21st century. Work: 70-80% of jobs will disappear in the next 20 years. There will be a lot of new jobs, but it is not clear if there will be enough new jobs in such a small time. Agriculture: There will be a $100 agricultural robot in the future. Farmers in 3rd world countries can then become managers of their field instead of working all day on their fields. Aeroponics will need much less water. The first Petri dish that produced veal is now available and will be cheaper than cow produced veal in 2018. Right now, 30% of all agricultural surfaces is used for cows. Imagine if we don't need that space anymore. There are several startups who will bring insect protein to the market shortly.. It contains more protein than meat. It will be labeled as "alternative protein source" (because most people still reject the idea of eating insects). There is an app called "moodies" which can already tell in which mood you're in. By 2020 there will be apps that can tell by your facial expressions, if you are lying. Imagine a political debate where it's being displayed when they're telling the truth and when they're not. Bitcoin may even become the default reserve currency... Of the world! Longevity: Right now, the average life span increases by 3 months per year. Four years ago, the life span used to be 79 years, now it's 80 years. The increase itself is increasing and by 2036, there will be more than one year increase per year. So, we all might live for a long time, probably way more than 100. Education: The cheapest smart phones are already at $10 in Africa and Asia. By 2020, 70% of all humans will own a smart phone. That means, everyone has the same access to world class education. Every child can use Khan academy for everything a child needs to learn at school in First World countries. There have already been releases of software in Indonesia and soon there will be releases in Arabic, Swahili, and Chinese this summer. I can see enormous potential if we give the English app for free, so that children in Africa and everywhere else can become fluent in English. And that could happen within half a year. ++++++++++++++++++++++++++++++++++ Another fascinating presentation: Dr. Dieter Zetsche, Chairman of the Board of Management of Daimler AG and Head of Mercedes-Benz Cars “Daimler 2017: Daimler and the transformation of the automotive industry" Annual Shareholders’ Meeting of Daimler AG Berlin March 29, 2017
Monday, December 11, 2017
An interesting article about the future and it is kinda scary
Thursday, December 7, 2017
New and old SEO techniques
relic of the
ancient past: keyword stuffing
Keyword stuffing has stopped working
years ago. Unfortunately, still use this technique. You've probably
seen web pages with content like this:
Search engine can detect that the sole purpose of the text above was to mention the term 'blue widget' as often as possible. It's also obvious that the text has not been written for human visitors. Modern search engine algorithms aren't stupid. If you're lucky, search engines will ignore your page. If you're not lucky, your website will get a penalty.
In addition, people who come to your website won't read this text. That also means that these people won't buy something from your website and they won't share the page on social networks.
In short: keyword stuffing is bad for your search engine rankings and it is bad for conversions.
"Buy blue
widgets for your friend. A blue widget is cool so order it for
yourself. With blue widgets, you will have tons of blue widget fun.
Enjoy your blue widget and get it from our blue widget shop. We have
everything for blue widgets."
Why is keyword
stuffing bad?Search engine can detect that the sole purpose of the text above was to mention the term 'blue widget' as often as possible. It's also obvious that the text has not been written for human visitors. Modern search engine algorithms aren't stupid. If you're lucky, search engines will ignore your page. If you're not lucky, your website will get a penalty.
In addition, people who come to your website won't read this text. That also means that these people won't buy something from your website and they won't share the page on social networks.
In short: keyword stuffing is bad for your search engine rankings and it is bad for conversions.

The better
alternative
Of course, your web pages still must
contain keywords that are related to the topic of your website.
Otherwise, search engines wouldn't be able to find out what your
website is about.
Modern search engine algorithms can detect topics. They know that the words 'sneakers' and 'footwear' are related to the keyword 'shoes'. If you want to optimize your website for keywords that are related to the topic 'shoes', write web page content that for human readers.
Convince your website visitors that your page is the right page for the topic and that the page contains the solution to their question. If you use your keywords in a natural context, search engines will find your web pages relevant to these keywords.
The Top 10 Optimizer tool in SEOprofiler helps you to optimize your web pages for keywords that are related to the topic of your website. You get detailed advice that is tailored to your situation:
Keywords are still very useful and I use them and recommend that you do especially keyword phrases but the day f putting in dog in a search is really over, you must be specific.
More to come soon.
Joe
Modern search engine algorithms can detect topics. They know that the words 'sneakers' and 'footwear' are related to the keyword 'shoes'. If you want to optimize your website for keywords that are related to the topic 'shoes', write web page content that for human readers.
Convince your website visitors that your page is the right page for the topic and that the page contains the solution to their question. If you use your keywords in a natural context, search engines will find your web pages relevant to these keywords.
The Top 10 Optimizer tool in SEOprofiler helps you to optimize your web pages for keywords that are related to the topic of your website. You get detailed advice that is tailored to your situation:
Keywords are still very useful and I use them and recommend that you do especially keyword phrases but the day f putting in dog in a search is really over, you must be specific.
More to come soon.
Joe
Wednesday, December 6, 2017
What does Rossini Management Systems do for our support customers
For our advanced support customers this is what we do for them:
We post to their Face book
We post to their Twitter
We post to their G+
We post to their LinkedIN
We post to their blog
We submit their web page to the top search engines
We give them a quick report analysis about their web site
And a whole lot more................................................................
Become a Rossini Management System customer and get the above and more from us!
More to come...
Joe Rossini
We post to their Face book
We post to their Twitter
We post to their G+
We post to their LinkedIN
We post to their blog
We submit their web page to the top search engines
We give them a quick report analysis about their web site
And a whole lot more................................................................
Become a Rossini Management System customer and get the above and more from us!
More to come...
Joe Rossini
Tuesday, November 28, 2017
Black Friday and Cyber Monday sales
The online sales holiday raked in $6.6 billion — up 17% over last year — and showed the rising force of mobile in digital holiday sales!
Retailers brought in nearly $6.6 billion, according to Adobe, which tracks data through its analytics services. That sales figure is up 16.8% compared to last year and is projected to be the largest online shopping day in history, Adobe said in a release.
Those figures are roughly in line with projections and represent a more than $2.5 billion increase since 2014, according to Adobe.
In many ways, it reflects the growth of e-commerce as an industry and as Cyber Monday has grown, digital sales have exploded throughout the entire Thanksgiving week as brick-and-mortar sales inch along or decline (but still remain hugely important to holiday sales).
Retail Dive took a look at some of the big takeaways from the day.
Mobile set a new record with 47.4% of site visits, with smartphones making up about 40% of visits, according to Adobe. Perhaps more importantly, Adobe said mobile accounted for 33.1% of Cyber Monday revenue (smartphones specifically accounted for 24.1% of revenue). Smartphone traffic specifically grew 22.2% year-over-year, while revenue coming from smartphones — at $1.59 billion on Monday — grew 39.2% percent year-over-year, marking a new all-time high.
"Shopping and buying on smartphones is becoming the new norm and can be attributed to continued optimizations in the retail experience on mobile devices and platforms," Mickey Mericle, vice president, marketing and customer insights at Adobe, said in a statement emailed to Retail Dive. "Consumers are also becoming more savvy and efficient online shoppers. People increasingly know where to find the best deals and what they want to purchase, which results in less price matching behavior typically done on desktops."
Rob Garf, vice president of industry strategy and insights with Salesforce's Commerce Cloud unit, said in an interview on Monday morning that computers' share of purchases over the shopping period fell below 50% for the first time.
Mobile accounted for 64% of Cyber Monday sales with merchants using Shopify's e-commerce platforms, according to Shopify. That was a 10% increase from last year.
The shift to mobile follows both the adoption of the smartphone over the past decade as well as retailers' (typically larger ones) efforts to make mobile shopping seamless and painless. And that goes not just for browsing, but purchasing. "Consumers are tethered to their mobile devices," Garf said. "They don't need to wait. Retailers have made it easier to purchase on their mobile device."
Mobile is king!!! More to xome soon.
From Joe Rossini
credit Retail Dive for the information
Retailers brought in nearly $6.6 billion, according to Adobe, which tracks data through its analytics services. That sales figure is up 16.8% compared to last year and is projected to be the largest online shopping day in history, Adobe said in a release.
Those figures are roughly in line with projections and represent a more than $2.5 billion increase since 2014, according to Adobe.
In many ways, it reflects the growth of e-commerce as an industry and as Cyber Monday has grown, digital sales have exploded throughout the entire Thanksgiving week as brick-and-mortar sales inch along or decline (but still remain hugely important to holiday sales).
Retail Dive took a look at some of the big takeaways from the day.
Mobile is taking over
"Mobile Monday" might soon be the better term for the day just passed, which the National Retail Federation dubbed Cyber Monday in 2005. More consumers than ever took to their phones to snatch up holiday sales deals, according to several firms tracking the day.Mobile set a new record with 47.4% of site visits, with smartphones making up about 40% of visits, according to Adobe. Perhaps more importantly, Adobe said mobile accounted for 33.1% of Cyber Monday revenue (smartphones specifically accounted for 24.1% of revenue). Smartphone traffic specifically grew 22.2% year-over-year, while revenue coming from smartphones — at $1.59 billion on Monday — grew 39.2% percent year-over-year, marking a new all-time high.
"Shopping and buying on smartphones is becoming the new norm and can be attributed to continued optimizations in the retail experience on mobile devices and platforms," Mickey Mericle, vice president, marketing and customer insights at Adobe, said in a statement emailed to Retail Dive. "Consumers are also becoming more savvy and efficient online shoppers. People increasingly know where to find the best deals and what they want to purchase, which results in less price matching behavior typically done on desktops."
Rob Garf, vice president of industry strategy and insights with Salesforce's Commerce Cloud unit, said in an interview on Monday morning that computers' share of purchases over the shopping period fell below 50% for the first time.
Mobile accounted for 64% of Cyber Monday sales with merchants using Shopify's e-commerce platforms, according to Shopify. That was a 10% increase from last year.
The shift to mobile follows both the adoption of the smartphone over the past decade as well as retailers' (typically larger ones) efforts to make mobile shopping seamless and painless. And that goes not just for browsing, but purchasing. "Consumers are tethered to their mobile devices," Garf said. "They don't need to wait. Retailers have made it easier to purchase on their mobile device."
Mobile is king!!! More to xome soon.
From Joe Rossini
credit Retail Dive for the information
Google BOT
What is Googlebot?
Googlebot is the name of Google's web
crawler. A web crawler is an automated program that systematically
browses the Internet for new web pages. This is called web-indexing or
web-spidering.
Google and other search engines use web crawlers to update their search indexes. Each search engine that has its own index also has its own web crawler. If you want to see your web pages on Google's search result pages, Googlebot has to visit your pages first.
Google has several bots: Googlebot (desktop), Googlebot (mobile), Googlebot Video, Googlebot Images, Googlebot News. For most websites, the Googlebots for desktop and mobile are the most important bots.
How does
Googlebot work?Google and other search engines use web crawlers to update their search indexes. Each search engine that has its own index also has its own web crawler. If you want to see your web pages on Google's search result pages, Googlebot has to visit your pages first.
Google has several bots: Googlebot (desktop), Googlebot (mobile), Googlebot Video, Googlebot Images, Googlebot News. For most websites, the Googlebots for desktop and mobile are the most important bots.
Basically, Googlebot and other web
crawlers follow the links that they find on web pages. If Googlebot
finds new links on a page, they will be added to the list of pages that
will be visited next. If a link does not work anymore, or if there is
new content on a web page, Google will update the index.
Googlebot uses sitemaps and databases of links discovered during previous crawls to determine where to go next. Whenever the crawler finds new links on a site, it adds them to the list of pages to visit next. If Googlebot finds changes in the links or broken links, it will make a note of that so the index can be updated. If you want to get good rankings on Google, you must make sure that Googlebot can correctly index your web pages. If web crawlers can easily crawl your web pages, you will get better results.
How to check the
crawlability of your web pagesGooglebot uses sitemaps and databases of links discovered during previous crawls to determine where to go next. Whenever the crawler finds new links on a site, it adds them to the list of pages to visit next. If Googlebot finds changes in the links or broken links, it will make a note of that so the index can be updated. If you want to get good rankings on Google, you must make sure that Googlebot can correctly index your web pages. If web crawlers can easily crawl your web pages, you will get better results.
If your web pages contain errors that
prevent Googlebot and other web crawlers from indexing them, you cannot
get high rankings. For that reason, it is important that you check the
crawlability of your web pages.
Keep making changes to your web site and let us make sure Google crawls your site.
Info from Google and Alandra
Keep making changes to your web site and let us make sure Google crawls your site.
Info from Google and Alandra
Wednesday, November 15, 2017
Robots are here where is the terminator
From CNN
Robots have already cost millions of factory jobs across the nation.
Next up could be jobs at your local stores.
Between 6 million to 7.5 million existing jobs are at risk of being replaced over the course of the next 10 years by some form of automation, according to a new study this week from by financial services firm Cornerstone Capital Group.
That represents at least 38% of the current retail work force, which consists of 16 million workers. Retail could actually lose a greater proportion of jobs to automation than manufacturing has, according to the study.
That doesn't mean that robots will be roving the aisles of your local department store chatting with customers. Instead, expect to see more automated checkout lines instead of cashiers. This shift alone will likely eliminate millions of jobs.
"Cashiers are considered one of the most easily automatable jobs in the economy," said the report. And these job losses will hit women particularly hard, since about 73% of cashiers are women.
There will also be fewer sales jobs, as more and more consumers use in-store smartphones and touchscreen computers to find what they need, said John Wilson, head of research at Cornerstone. There will still be some sales people on the floor, but just not as many of them.
Monday, November 6, 2017
From SEJ a neat article
According to estimates from Statista, by the end of 2017, there will be around 2.7 billion social media users in the world – a figure that is expected to rise by about 7 percent each year.
This fact alone should cause all social media marketers to sit up and consider the opportunities for their own marketing campaigns.
But let’s be honest.
While opportunities abound, social media marketing is complicated.
Targeting the social media crowd is like targeting a moveable feast. It is never static.
People come and go quickly in social media and their interests change from one day to the next.
So, before you invest heavily in any social media marketing campaign, you really need to understand the landscape.
The rewards can be high and also immediate if you strike the right note with your target audience. Miss the target and you could exhaust your social media budget very quickly.
And, while it’s important to build relationships with a social media environment, you must remember that relationship building is simply a strategy it is not the end goal. Foremost business the end goal of any social media marketing strategy is to boost engagement and increase conversions.
You may be well branded, you may be well-known, but if you are not increasing the bottom line through your social media marketing, then you cannot really justify the investment
More to come shortly!~
Joe Rossini
This fact alone should cause all social media marketers to sit up and consider the opportunities for their own marketing campaigns.
But let’s be honest.
While opportunities abound, social media marketing is complicated.
Targeting the social media crowd is like targeting a moveable feast. It is never static.
People come and go quickly in social media and their interests change from one day to the next.
So, before you invest heavily in any social media marketing campaign, you really need to understand the landscape.
The rewards can be high and also immediate if you strike the right note with your target audience. Miss the target and you could exhaust your social media budget very quickly.
And, while it’s important to build relationships with a social media environment, you must remember that relationship building is simply a strategy it is not the end goal. Foremost business the end goal of any social media marketing strategy is to boost engagement and increase conversions.
You may be well branded, you may be well-known, but if you are not increasing the bottom line through your social media marketing, then you cannot really justify the investment
More to come shortly!~
Joe Rossini
Interesting from Google
Just a quick snippet from Google:
Google has announced plans to introduce local display ads for highlighting in-store products and sales.
Unlike other Google ads, which typically spotlight products and services that can be ordered online, local display ads promote goods that can be acquired at brick and mortar locations.
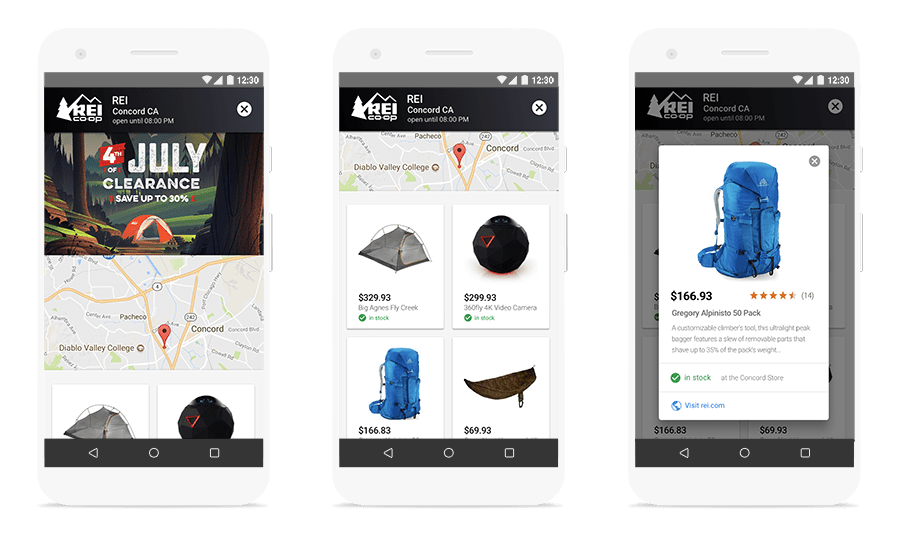
Rather than driving online traffic, the goal of local display ads is to drive more foot traffic.
In order to run local display ads you must first have a local inventory feed set up for shopping ads.
Google has announced plans to introduce local display ads for highlighting in-store products and sales.
Unlike other Google ads, which typically spotlight products and services that can be ordered online, local display ads promote goods that can be acquired at brick and mortar locations.

Rather than driving online traffic, the goal of local display ads is to drive more foot traffic.
In order to run local display ads you must first have a local inventory feed set up for shopping ads.
Thursday, November 2, 2017
Should we be afraid of robots?
Here is a nice article about robots and surprisingly they are not replacing humans just helping them:
There are also many AI applications that have already moved from research to employment in facilities around the world. Self-navigating industrial vehicles, although still an area of research, are already in many warehouses (continued research will serve to increase their capabilities). Omron’s mobile robot, Adept, for instance, will automatically drive to desired locations once it has mapped a facility. With the ability to grab objects of different shapes, there are even some robotic grippers that are already employing a portion of the technology being researched by the Berkley group. Clearly, then, AI has had a substantial effect on material handling automation, and with continued research, it will continue to shape it. Does this mean we can expect a future where distribution centers and manufacturing facilities are totally automated, i.e. without any human workers? Perhaps, but probably not.
To date, AI has increased the capabilities of material handling automation, and automation, in turn, has made workers more productive and valuable. Thus, in my experience, after automating a process, companies do not eliminate workers. Rather, those workers become much more productive or are moved into a different process that provides more value. For example, a goods-to-person system such as AutoStore will drastically increase the number of items a human picker can pick, so the human is not replaced, but is now much more productive. Eventually, I do think that researchers like those at Berkley will create systems that replace the human picker in this process, but that person will not go away. Machines are not perfect, and humans will need to supervise them and correct them when they make mistakes. The picker, therefore, will become a supervisor of intelligent machines, taking immediate corrective action when the machines make mistakes in order to keep production moving.
More to come.
Artificial Intelligence in Material Handling
Research into AI is well funded and progressing quickly in the material handling arena. As reported by the NY Times, researchers in Berkley, for instance, are working on robots that can look inside a bin full of randomly sized objects, quickly understand the size and shape of each discrete item, and then successfully grab one and place it in a desired location. This type of behavior has always been outside the capability of robots, requiring companies to hire human “pickers” to perform it. Other areas of research include self-navigating autonomous industrial vehicles (e.g. AGVs and fork trucks), using AI to optimize material flow in a facility, predictive maintenance for material handling components, and many more.There are also many AI applications that have already moved from research to employment in facilities around the world. Self-navigating industrial vehicles, although still an area of research, are already in many warehouses (continued research will serve to increase their capabilities). Omron’s mobile robot, Adept, for instance, will automatically drive to desired locations once it has mapped a facility. With the ability to grab objects of different shapes, there are even some robotic grippers that are already employing a portion of the technology being researched by the Berkley group. Clearly, then, AI has had a substantial effect on material handling automation, and with continued research, it will continue to shape it. Does this mean we can expect a future where distribution centers and manufacturing facilities are totally automated, i.e. without any human workers? Perhaps, but probably not.
To date, AI has increased the capabilities of material handling automation, and automation, in turn, has made workers more productive and valuable. Thus, in my experience, after automating a process, companies do not eliminate workers. Rather, those workers become much more productive or are moved into a different process that provides more value. For example, a goods-to-person system such as AutoStore will drastically increase the number of items a human picker can pick, so the human is not replaced, but is now much more productive. Eventually, I do think that researchers like those at Berkley will create systems that replace the human picker in this process, but that person will not go away. Machines are not perfect, and humans will need to supervise them and correct them when they make mistakes. The picker, therefore, will become a supervisor of intelligent machines, taking immediate corrective action when the machines make mistakes in order to keep production moving.
More to come.
Tuesday, October 31, 2017
What I have been saying all along read this!
Search engine optimization is about getting clicks from the right people, not about rankings
Getting high rankings on search engines can be very difficult. It is important that you have a plan before you start to optimize your web pages and links. It's not enough to get traffic to your website. It is very important that your web pages get targeted traffic. Search engine optimization is not about getting high rankings. It is about getting clicks from the right people.
Don't waste your time on untargeted traffic
In the early days of the Internet, people participated in traffic exchange programs. You joined a network of websites that opened pop-under windows that contained a link to your website. Your website would get thousands of visitors within a few days.
Unfortunately, none of these 'visitors' would buy something on your website. Although these traffic exchange programs still exist, most website owners have understood that these programs were pointless. However, a lot of business owners still try to get high rankings for the wrong keywords.
Unfortunately, none of these 'visitors' would buy something on your website. Although these traffic exchange programs still exist, most website owners have understood that these programs were pointless. However, a lot of business owners still try to get high rankings for the wrong keywords.
Get more targeted traffic: focus on the right keywords
If your website has high rankings for the wrong keywords, you won't get targeted traffic. It does not make sense to get high rankings for a keyword that seems to be related but does not deliver people who are interested to buy.
For example, "car" is an extremely popular keyword. If you manage to get high rankings for the search term "car" then your website will get thousands of visitors per day. Of course, you will also have to invest months into getting your website on the first result page for that single term.
However, you won't get many sales from people who find your website through that keyword. People who search for "car" might be interested in anything that is related to cars: general information, car tuning, car repair parts, tires, news, images, etc. If you are selling products for auto cockpit cleaning on your website then most of these visitors won't buy.
It is important that you concentrate on targeted keywords that deliver targeted traffic (for example "auto cockpit cleaning", "car dashboard cleaning", etc.). It is much easier to get high rankings for these keywords, and you will get many more sales from these high rankings (From seo profiler).
More info snippets to come soon.
Joe Rossini
For example, "car" is an extremely popular keyword. If you manage to get high rankings for the search term "car" then your website will get thousands of visitors per day. Of course, you will also have to invest months into getting your website on the first result page for that single term.
However, you won't get many sales from people who find your website through that keyword. People who search for "car" might be interested in anything that is related to cars: general information, car tuning, car repair parts, tires, news, images, etc. If you are selling products for auto cockpit cleaning on your website then most of these visitors won't buy.
It is important that you concentrate on targeted keywords that deliver targeted traffic (for example "auto cockpit cleaning", "car dashboard cleaning", etc.). It is much easier to get high rankings for these keywords, and you will get many more sales from these high rankings (From seo profiler).
More info snippets to come soon.
Joe Rossini
More info from Google
The guides describe Google's standard
for their own content. It's very likely that Google will think that
your web pages are high-quality pages if they meet these standards.
Here are some key points from the documents:
Recommendations for your content:
Recommendations for your content:
- Aim for a voice and tone that's conversational, friendly, and respectful without being overly colloquial or frivolous; a voice that's casual and natural and approachable, not pedantic or pushy. Try to sound like a knowledgeable friend who understands what the reader wants to do.
- Use standard spelling, grammar, punctuation and capitalization. Write short and concise sentences that are easy to understand.
- Use descriptive link texts, i.e. "download the user manual" instead of "click here". If you link to other websites, make sure that these websites are reliable and respectable.
- Avoid buzzwords and technical jargon. Don't use exclamation marks, except in rare really exciting moments.
- Consider numbered lists and bullet lists to structure your content.
As I have always said, content is King so have it it is important. Ok Back to Google speak:)
How to optimize
your pages
There are many things to consider if you want to get high rankings on Google and other search engines. In addition to the things above, you should check your pages for other technical things that can have a negative influence on your rankings. After that, optimize your pages so that they get high rankings for the right keywords.
Long tail keywords are important, ask your SEO specialist "like me" to help you with your SEO and your keywords.
Google: do not remove old content or archived news stories
There are many things to consider if you want to get high rankings on Google and other search engines. In addition to the things above, you should check your pages for other technical things that can have a negative influence on your rankings. After that, optimize your pages so that they get high rankings for the right keywords.
Long tail keywords are important, ask your SEO specialist "like me" to help you with your SEO and your keywords.
Google: do not remove old content or archived news stories
"It
has become a trend by SEOs
to remove older content, especially older content on a news sites,
where sites remove content rather than simply archiving it. [...]
Gary Illyes from Google [...] had an explicit warning – if you remove this older content, you will lose traffic [...] You can redirect that page somewhere, which would be more relevant in your mind, but I typically disagree with that as well, just like you for the same reasons."
Gary Illyes from Google [...] had an explicit warning – if you remove this older content, you will lose traffic [...] You can redirect that page somewhere, which would be more relevant in your mind, but I typically disagree with that as well, just like you for the same reasons."
Here we go again another update on Google:
Google
search algorithm update coming?
"We
are seeing quite wild swings
across all sites. I know there are quite a lot of these predictions
around here these days, and yes i do appreciate that updates are
happening almost all the time (thank you very much) but this does look
like some sort of "larger than a normal day" type update."
Ok more to come soon.
Joe Rossini
Thursday, October 12, 2017
More facts about cyber security and it is scary!
Social media – a hackers’ favorite target
Currently, according to in depth statistics, there are more than 1.6 billion social network users worldwide with more than 64% of internet users accessing social media services online. Moreover, social networking is one of the most popular ways for online users to spend their time, and a preferred way to stay in contact with friends and families.
This is precisely why cyber attackers love social media as well! Users that spend a lot of time on social networks are very likely to click links posted by trusted friends, which hackers use to their advantage. Here are some of the most popular types of cyber attacks directed at social media platforms:
- Like-jacking: occurs when criminals post fake Facebook “like” buttons to webpages. Users who click the button don’t “like” the page, but instead download malware.
- Link-jacking: this is a practice used to redirect one website’s links to another which hackers use to redirect users from trusted websites to malware infected websites that hide drive-by downloads or other types of infections.
- Phishing: the attempt to acquire sensitive information such as usernames, passwords, and credit card details (and sometimes, indirectly, money) by disguising itself as a trustworthy entity in a Facebook message or Tweet.
- Social spam: is unwanted spam content appearing on social networks and any website with user-generated content (comments, chat, etc.). It can appear in many forms, including bulk messages, profanity, insults, hate speech, malicious links, fraudulent reviews, fake friends, and personally identifiable information.

Why are cyber attacks on social media so frequent?
Because social media users usually trust their circles of online friends. The result: more than 600.000 Facebook accounts are compromised every single day! Also, 1 in 10 social media users said they’ve been a victim of a cyber attack and the numbers are on the rise. Now this is a cyber security statistic which we don’t want you to become part of.
How it affects you and what can you do to get protected:
- Don’t click any strange links.
- This is courtesy of HEIMDAL.
Tuesday, October 10, 2017
How is retail going to do this holiday season?
This is what some experts are saying about this coming holiday season:
http://www.retaildive.com/news/holiday-sales-growth-dependent-on-high-income-online-shoppers/506460/
http://www.retaildive.com/news/holiday-sales-growth-dependent-on-high-income-online-shoppers/506460/
Friday, October 6, 2017
Secure your systems
To follow is just a quick look at securing your systems. Today threats are everywhere so be vigilant!
Prevent Network Intrusions with Multiple Strategies
A complete network overhaul isn’t always necessary to improve security. Many providers offer easy-to-deploy network solutions that incorporate powerful security features.
Firewalls built into routers, for example, allow IT staff to monitor incoming and outgoing network traffic and decide whether to allow or block specific traffic based on a defined set of security rules. A proven and reliable network security technology, firewalls create a barrier between secure internal networks and untrusted external networks, such as the internet.
“Leverage next-generation firewalls,” Gheri recommends. “These devices can identify traffic based on applications. And good next-generation firewalls can apply different traffic optimization techniques to different kinds of application traffic.”
An intrusion prevention system (IPS), implemented either as a device or through software, is a powerful tool that examines traffic flows to detect and block vulnerability exploits, an approach attackers frequently use to access or cripple an application.
Intrusion prevention is a standard feature in most next-generation firewalls. “It provides base-line security, but be aware that an IPS should not have a blind spot regarding SSL-encrypted traffic,” Gheri warns. “Encrypted traffic needs to be decrypted and then matched against malware signatures and payload needs to be inspected for advanced malware.”
Segmentation, a technique widely supported by network technology providers, splits a network into multiple subnetworks, commonly known as segments. The approach allows organizations to group applications and related data together for access only by specific users (such as sales or finance staff). This technique can also be used to restrict the range of access provided to a particular user.
Segmentation is perhaps the simplest way to improve an organization’s security posture, since using network address segments to control access hampers cyber attackers. “It can also help to contain malware outbreaks,”
info by viztech
Tuesday, October 3, 2017
What Amazon is thinking for the future and it is well unusual
I want you to read this it is funky and well shows you what the big boy is thinking:
http://www.techgistics.net/blog/2017/9/28/connecting-the-dots-on-amazons-patents-in-logistics
More to come soon.
Joe Rossini
http://www.techgistics.net/blog/2017/9/28/connecting-the-dots-on-amazons-patents-in-logistics
More to come soon.
Joe Rossini
Monday, October 2, 2017
The top 10 e commerce retailers distribution facilities
The 10 Retailers With the Most E-Commerce Distribution Centers
Digital retailing is tough. Not only do retailers need to find innovative ways to drive traffic to their sites and induce a sale, they need to be able to fulfill any and all orders at breakneck speed. Customers are making purchase decisions based on delivery times and the more DCs a retailer has the better its chances of meeting shopper expectations.
In its Top 500 Guide Internet Retailer ranks the top e-commerce retailers across numerous metrics including number of fulfillment centers. The entire report is available here, and a quick look at the 10 retailers with the most DCs is below.
Amazon. No surprise here that Amazon tops the list, nearly tripling second place finisher IKEA. Amazon has fulfillment centers in 19 states, to help process the 350 million SKUs the online giant carries. Number of e-Commerce Distribution Centers: 109.
IKEA. While the furniture retailer is known for its sprawling, warehouse-like showrooms, over $134 million of its revenue comes from web-based sales. In fact, IKEA's web sales increased 25% in 2015, with eight million monthly visitors. Number of e-Commerce Distribution Centers: 39.
O'Reilly Auto Parts. O'Reilly is growing not only its physical footprint as it looks to enter the lucrative northeast market, but its only presence as well. The auto parts retailer's web sales increase 14% last year and not account for over $176 million in revenue. Number of e-Commerce Distribution Centers: 23.
W.W. Grainger. The hardware and home improvement retailer stocks over 1.4 million SKUs. It has over 9 million visitors browse its site each month — a huge jump from the 4.5 million that visited each month in 2014. Number of e-Commerce Distribution Centers: 18.
Safeway Inc. While digital grocery sales are still in their infantcy many of the nation's top supermarket chain have made significant investment in the space. Safeway's web sales have been relatively flat year-over-year, but it still accounts for nearly $230 million in revenue. Number of e-Commerce Distribution Centers: 17.
Bed Bath & Beyond. The New Jersey-based home goods retailer continues to scale up its digital shopping efforts, with web sales increasing 25% year-over-year. The retailer is investing heavily in the mobile experience to capture busy on-the-go shoppers. Number of e-Commerce Distribution Centers: 17.
Sears Hometown/Outlets. The retailer operates two brands, Sears Hometown and Hardware storea nad the Sears Outlet Stores, with revenues north of $325 million. It sells home appliances, lawn and garden equipment, tool and hardware, and has fulfillment centers located in 10 states. Number of e-Commerce Distribution Centers: 16.
Estee Lauder. The cosmetics and fragrance manufacturer and retailer have over 8.6 million monthly visitors, and sports a 4% conversion rate. Its web sales have been growing by leaps and bounds, increasing to over $860 million in 2015, an increase of nearly 28% from 2014's total. Number of e-Commerce Distribution Centers: 14.
GameStop Corp. With the vast majority of its shoppers 34 years old and younger the video game retailer has a massive digital presence. Web sales topped the $1 billion mark in 2015, representing a 25% bump over 2014 totals. Number of e-Commerce Distribution Centers: 13.
Systemax. The industrial supplies, computers and electronics supplies retailer has web sales north of $1.4 billion, and hosts 3.7 million unique visitors per month. It sells over 450,000 SKUs and an average ticket value of $440. Number of e-Commerce Distribution Centers: 13.
In its Top 500 Guide Internet Retailer ranks the top e-commerce retailers across numerous metrics including number of fulfillment centers. The entire report is available here, and a quick look at the 10 retailers with the most DCs is below.
Amazon. No surprise here that Amazon tops the list, nearly tripling second place finisher IKEA. Amazon has fulfillment centers in 19 states, to help process the 350 million SKUs the online giant carries. Number of e-Commerce Distribution Centers: 109.
IKEA. While the furniture retailer is known for its sprawling, warehouse-like showrooms, over $134 million of its revenue comes from web-based sales. In fact, IKEA's web sales increased 25% in 2015, with eight million monthly visitors. Number of e-Commerce Distribution Centers: 39.
O'Reilly Auto Parts. O'Reilly is growing not only its physical footprint as it looks to enter the lucrative northeast market, but its only presence as well. The auto parts retailer's web sales increase 14% last year and not account for over $176 million in revenue. Number of e-Commerce Distribution Centers: 23.
W.W. Grainger. The hardware and home improvement retailer stocks over 1.4 million SKUs. It has over 9 million visitors browse its site each month — a huge jump from the 4.5 million that visited each month in 2014. Number of e-Commerce Distribution Centers: 18.
Safeway Inc. While digital grocery sales are still in their infantcy many of the nation's top supermarket chain have made significant investment in the space. Safeway's web sales have been relatively flat year-over-year, but it still accounts for nearly $230 million in revenue. Number of e-Commerce Distribution Centers: 17.
Bed Bath & Beyond. The New Jersey-based home goods retailer continues to scale up its digital shopping efforts, with web sales increasing 25% year-over-year. The retailer is investing heavily in the mobile experience to capture busy on-the-go shoppers. Number of e-Commerce Distribution Centers: 17.
Sears Hometown/Outlets. The retailer operates two brands, Sears Hometown and Hardware storea nad the Sears Outlet Stores, with revenues north of $325 million. It sells home appliances, lawn and garden equipment, tool and hardware, and has fulfillment centers located in 10 states. Number of e-Commerce Distribution Centers: 16.
Estee Lauder. The cosmetics and fragrance manufacturer and retailer have over 8.6 million monthly visitors, and sports a 4% conversion rate. Its web sales have been growing by leaps and bounds, increasing to over $860 million in 2015, an increase of nearly 28% from 2014's total. Number of e-Commerce Distribution Centers: 14.
GameStop Corp. With the vast majority of its shoppers 34 years old and younger the video game retailer has a massive digital presence. Web sales topped the $1 billion mark in 2015, representing a 25% bump over 2014 totals. Number of e-Commerce Distribution Centers: 13.
Systemax. The industrial supplies, computers and electronics supplies retailer has web sales north of $1.4 billion, and hosts 3.7 million unique visitors per month. It sells over 450,000 SKUs and an average ticket value of $440. Number of e-Commerce Distribution Centers: 13.
Tuesday, September 26, 2017
Company cyber security and why we are at risk!
To follow are parts of articles written by SolarWinds MSP:
Companies are overlooking seven basic security principles: 1. Security policies are inconsistently applied. 2. User training is massively under-prioritized. 3. Only basic technologies are being deployed. 4. Vulnerability reporting is often weak, or even nonexistent. 5. The majority of organizations make no changes to their technology or processes following a breach. 6. Widely accepted prevention techniques and processes remain overlooked. 7. Detection, response, and resolution times are all growing.
Did you know that:
77% of respondents reported tangible loss (monetary, legal action, loss of customer) from a security incident 23% of survey respondents reported intangible loss (of brand reputation, etc)
So, in hard commercial terms, what does this vulnerability cost a typical SMB or enterprise? Beyond the readily identifiable impacts of a lost customer or downtime leading to lost opportunity, what are the wider implications? In their “2016 Cost of Data Breach Study: Global Analysis,” 1 IBM and Ponemon calculated a standard cost per lost or stolen record of USD $158/ GBP £122. This calculation included direct expenses (e.g. engaging forensic experts, outsourcing hotline support, and customer relationship remedial costs such as discounts on products and services) and indirect costs (in-house investigations and internal communications). It also extrapolated typical values of lost customers and the impact of brand damage on future customer acquisition. This may not seem like a lot but $158.00 x tens of thousanmds and now you see what they mean! I have often heard that hackers go into banks mostly small banks and they dont steal thousands but maybe $1.00 or less! Tink if you did this to thousands of banks and once again you see a lot of loss. Banks will not do much for a loss of that size so the hackers come back and back until they are stopped!
Based directly on our research, the following represent the top seven pitfalls that are opening UK and US businesses up to massive financial liabilities, with the potential for something as serious as an extinction event. 1. INCONSISTENCY IN ENFORCING SECURITY POLICIES A security policy is clearly worthless unless it is correctly enforced and its suitability is regularly checked. However, only 32% of respondents could claim their security policies are reliably applied and regularly audited. On top of this, less than half or 43% enforce them only occasionally, 17% fail to audit their suitability, and 7% have no policies in place.
2. NEGLIGENCE IN THE APPROACH TO USER SECURITY AWARENESS TRAINING Despite all the commentary about its importance, only 16% of respondents considered user security awareness training a priority. A massive 71% pay lip service to it by either including security awareness as a one-off event at employee onboarding or reinforcing it once a year. The remainder, 13%, admitted they do nothing
3. SHORTSIGHTEDNESS IN THE APPLICATION OF CYBERSECURITY TECHNOLOGIES Six of the nine most typical cybersecurity technologies had been deployed by only a minority of respondents. Web protection, email scanning, and anti-malware had each been rolled out by 50-61%, but the remaining six (including SIEM, firewall rules, and patch management) had been deployed by only 33% at the most (SIEM), or 25% at the lowest (intrusion systems)
4. COMPLACENCY AROUND VULNERABILITY REPORTING Only 29% of respondents could call their vulnerability reporting robust, with the majority, 51%, optimistically classifying it as adequate. Surprisingly, as many as 19% have no reporting, and 11% even said they categorically had no plans to investigate its deployment or usefulness.
5. INFLEXIBILITY IN ADAPTING PROCESSES AND APPROACH AFTER A BREACH Following a breach (experienced by 71% of respondents), only 44% implemented new technology, and only 41% changed their processes. Meanwhile, 42% started looking into new technology, while 14% purposefully did nothing
6. STAGNATION I N T H E A P P L I C A T I O N O F K E Y P R E V E N T I O N T E C H N I Q U E S Of the nine key prevention techniques listed, only a minority of respondents had implemented all of them. The most prevalent technique was full disk encryption on mobile and portable endpoints, but even this was only performed by 43%. Application white listing was implemented by only 38%, and logging of authenticated users’ activity was used by only 41%.
7. LETHARGY AROUND DETECTION AND RESPONSE Over the past 12 months, detection times had risen for 40% of respondents; response times were up for 44%; and resolution times had increased for 46%. In contrast, in our 2016 report, detection times had risen for only 28% of respondents; response times were up for 28%; and resolution times had increased for 27%. This shows that the rate of decay (and complacency) is growing
ADVICE FOR MSPS The data and conclusions in this report make one crucial point overwhelmingly clear: Enterprises and SMBs alike are overconfident in their cybersecurity preparedness. This being the case, what opportunities do managed services providers (MSPs) have? Opportunity #1: Offer cybersecurity training to your customers. Training can make a huge difference in your clients’ security, so it’s absolutely essential that you arm them with the knowledge they need to prevent breaches. Whether you offer it as a service to build revenue or you offer it free to provide retention, training can cut down on the number of security incidents. That translates to fewer emergency calls and, ultimately, happier clients. Opportunity #2: Make sure your own house is in order. MSPs need to make sure their own security practices are up to par. You should review your practices and security technology stack not only for current best practices, but with an eye to the future as well. Does your security meet the current and future needs of the typical SMB or enterprise? Does it work well across on-premises, cloud, and hybrid environments? Can you serve clients in highly-regulated verticals? Opportunity #3: Prepare with disaster drills. MSPs can also offer to stress test their clients’ security via “war games.” Many industries run drills to help them deal with worst case scenarios: marketing teams practice their responses to PR crises, financial services organizations stress test their portfolios, and logistics teams plan for transportation hubs closing down unexpectedly. As an MSP, you can practice disaster events with your clients, both in terms of technology and processes, to discover weak points and make improvements. Are the lines of communication and equipment sufficiently robust? Are expectations and metrics reasonable? You’re likely to find a few upsell opportunities in the process. Opportunity #4: Determine the partnerships or skillsets you’ll need. Many security incidents require specialists to handle, so make sure to prepare before you need it. Whether it’s warding off DDoS attacks, protecting IoT at an architectural level, or implementing digital forensics incident response, you should either look to hire expertise in-house or partner with someone who can handle these for you. You never want to have to build new skills in the middle of a crisis. Organizations’ overconfidence combined with the prevalence of the seven pitfalls of cybersecurity create a perfect storm on which cybercriminals are bound to capitalize. But with the right approach, dialogue, relationships, and tools, MSPs can turn these flaws into lucrative opportunities. CYBERSECURITY: CAN OVERCONFIDENCE LEAD TO AN EXTINCTION EVENT? 1
I think that the above will happen. I worry about breaches to our national security, our infrastructure, our banks and more. Be prepared!!!
More to come from Joe Rossini
Companies are overlooking seven basic security principles: 1. Security policies are inconsistently applied. 2. User training is massively under-prioritized. 3. Only basic technologies are being deployed. 4. Vulnerability reporting is often weak, or even nonexistent. 5. The majority of organizations make no changes to their technology or processes following a breach. 6. Widely accepted prevention techniques and processes remain overlooked. 7. Detection, response, and resolution times are all growing.
Did you know that:
77% of respondents reported tangible loss (monetary, legal action, loss of customer) from a security incident 23% of survey respondents reported intangible loss (of brand reputation, etc)
So, in hard commercial terms, what does this vulnerability cost a typical SMB or enterprise? Beyond the readily identifiable impacts of a lost customer or downtime leading to lost opportunity, what are the wider implications? In their “2016 Cost of Data Breach Study: Global Analysis,” 1 IBM and Ponemon calculated a standard cost per lost or stolen record of USD $158/ GBP £122. This calculation included direct expenses (e.g. engaging forensic experts, outsourcing hotline support, and customer relationship remedial costs such as discounts on products and services) and indirect costs (in-house investigations and internal communications). It also extrapolated typical values of lost customers and the impact of brand damage on future customer acquisition. This may not seem like a lot but $158.00 x tens of thousanmds and now you see what they mean! I have often heard that hackers go into banks mostly small banks and they dont steal thousands but maybe $1.00 or less! Tink if you did this to thousands of banks and once again you see a lot of loss. Banks will not do much for a loss of that size so the hackers come back and back until they are stopped!
Based directly on our research, the following represent the top seven pitfalls that are opening UK and US businesses up to massive financial liabilities, with the potential for something as serious as an extinction event. 1. INCONSISTENCY IN ENFORCING SECURITY POLICIES A security policy is clearly worthless unless it is correctly enforced and its suitability is regularly checked. However, only 32% of respondents could claim their security policies are reliably applied and regularly audited. On top of this, less than half or 43% enforce them only occasionally, 17% fail to audit their suitability, and 7% have no policies in place.
2. NEGLIGENCE IN THE APPROACH TO USER SECURITY AWARENESS TRAINING Despite all the commentary about its importance, only 16% of respondents considered user security awareness training a priority. A massive 71% pay lip service to it by either including security awareness as a one-off event at employee onboarding or reinforcing it once a year. The remainder, 13%, admitted they do nothing
3. SHORTSIGHTEDNESS IN THE APPLICATION OF CYBERSECURITY TECHNOLOGIES Six of the nine most typical cybersecurity technologies had been deployed by only a minority of respondents. Web protection, email scanning, and anti-malware had each been rolled out by 50-61%, but the remaining six (including SIEM, firewall rules, and patch management) had been deployed by only 33% at the most (SIEM), or 25% at the lowest (intrusion systems)
4. COMPLACENCY AROUND VULNERABILITY REPORTING Only 29% of respondents could call their vulnerability reporting robust, with the majority, 51%, optimistically classifying it as adequate. Surprisingly, as many as 19% have no reporting, and 11% even said they categorically had no plans to investigate its deployment or usefulness.
5. INFLEXIBILITY IN ADAPTING PROCESSES AND APPROACH AFTER A BREACH Following a breach (experienced by 71% of respondents), only 44% implemented new technology, and only 41% changed their processes. Meanwhile, 42% started looking into new technology, while 14% purposefully did nothing
6. STAGNATION I N T H E A P P L I C A T I O N O F K E Y P R E V E N T I O N T E C H N I Q U E S Of the nine key prevention techniques listed, only a minority of respondents had implemented all of them. The most prevalent technique was full disk encryption on mobile and portable endpoints, but even this was only performed by 43%. Application white listing was implemented by only 38%, and logging of authenticated users’ activity was used by only 41%.
7. LETHARGY AROUND DETECTION AND RESPONSE Over the past 12 months, detection times had risen for 40% of respondents; response times were up for 44%; and resolution times had increased for 46%. In contrast, in our 2016 report, detection times had risen for only 28% of respondents; response times were up for 28%; and resolution times had increased for 27%. This shows that the rate of decay (and complacency) is growing
ADVICE FOR MSPS The data and conclusions in this report make one crucial point overwhelmingly clear: Enterprises and SMBs alike are overconfident in their cybersecurity preparedness. This being the case, what opportunities do managed services providers (MSPs) have? Opportunity #1: Offer cybersecurity training to your customers. Training can make a huge difference in your clients’ security, so it’s absolutely essential that you arm them with the knowledge they need to prevent breaches. Whether you offer it as a service to build revenue or you offer it free to provide retention, training can cut down on the number of security incidents. That translates to fewer emergency calls and, ultimately, happier clients. Opportunity #2: Make sure your own house is in order. MSPs need to make sure their own security practices are up to par. You should review your practices and security technology stack not only for current best practices, but with an eye to the future as well. Does your security meet the current and future needs of the typical SMB or enterprise? Does it work well across on-premises, cloud, and hybrid environments? Can you serve clients in highly-regulated verticals? Opportunity #3: Prepare with disaster drills. MSPs can also offer to stress test their clients’ security via “war games.” Many industries run drills to help them deal with worst case scenarios: marketing teams practice their responses to PR crises, financial services organizations stress test their portfolios, and logistics teams plan for transportation hubs closing down unexpectedly. As an MSP, you can practice disaster events with your clients, both in terms of technology and processes, to discover weak points and make improvements. Are the lines of communication and equipment sufficiently robust? Are expectations and metrics reasonable? You’re likely to find a few upsell opportunities in the process. Opportunity #4: Determine the partnerships or skillsets you’ll need. Many security incidents require specialists to handle, so make sure to prepare before you need it. Whether it’s warding off DDoS attacks, protecting IoT at an architectural level, or implementing digital forensics incident response, you should either look to hire expertise in-house or partner with someone who can handle these for you. You never want to have to build new skills in the middle of a crisis. Organizations’ overconfidence combined with the prevalence of the seven pitfalls of cybersecurity create a perfect storm on which cybercriminals are bound to capitalize. But with the right approach, dialogue, relationships, and tools, MSPs can turn these flaws into lucrative opportunities. CYBERSECURITY: CAN OVERCONFIDENCE LEAD TO AN EXTINCTION EVENT? 1
I think that the above will happen. I worry about breaches to our national security, our infrastructure, our banks and more. Be prepared!!!
More to come from Joe Rossini
Mobile e commerce is growing fast
Some info on mobile e commerce:
- Target is enhancing its mobile app with beacon and Bluetooth technology that shows a customer’s location on the app’s map as they move about the store, Target’s chief information and digital officer Mike McNamara said in a company blog post. In a video, he likened the technology to driving with GPS.
- Target's app will also point shoppers to nearby promotional prices, dubbed "Cartwheel" deals, for users of its mobile app. The new features are is set to go live in about half of Target’s stores for the holidays.
- The mapping capability comes a few weeks after Target began to move its Cartwheel savings app to its flagship mobile app.
- A new voice technology integration from Unata, an enabler of digital solutions for grocers, will allow grocery retailers to offer voice ordering to their customers, according to a press release.
- The new capability was developed in-house by Unata and can be used through a grocer's website or mobile app, a company spokeswoman told Retail Dive. Unata plans to showcase the voice ordering technology next week at the Shop.org Digital Retail Conference in Los Angeles.
- The technology supports a number of conversation-driven shopping interactions, including comprehensive list building, updates on sales and offers specialized for the shopper, placing orders, finding store information and more, according to the company.
Dive Brief:
- More millennial-age consumers visit multiple stores in search of deals than their baby boomer elders do, according to research from consumer engagement firm First Insight. Some 71% of millennials frequent a variety of stores, compared to 57% of baby boomers, according to a report emailed to Retail Dive.
- While most millennials do go online to search for deals (82%), the study found that same shopping behavior within both generational groups, as more baby boomers (65%), especially those with higher incomes, are also looking online for the best price rather than in-store, First Insight said.
- Most millennials (92%) this holiday season plan to spend money in a physical store, according to other research from the International Council of Shopping Centers, which is forecasting a 3.8% year-over-year growth in retail sales for the season. On average, they plan to spend $554.40 on holiday gifts and related items, according to an ICSC report emailed to Retail Dive.
There is no doubt to me that the use of mobile by all generations is up and that being able to be found is important.
More to come.
Joe Rossini
Tuesday, September 5, 2017
Mobile e commerce is it real and why you should be there!
5 Reasons to Get Ready Now
Over the last decade, people have come to use their mobile devices over all other devices to browse and shop on websites. Is your brand prepared for this new mobile-first world?
If you’re an e-com business, this is the most important question to answer today. Why? Because every day you don’t compete on mobile, you become a little less relevant among your customers.
Here’s what we’ll cover in this eBook:
If you’re an e-com business, this is the most important question to answer today. Why? Because every day you don’t compete on mobile, you become a little less relevant among your customers.
Here’s what we’ll cover in this eBook:
- Why retailers must have a strategy to tap into the monstrous growth of mobile sales.
- Mobile consumer data from Black Friday and what it means for retailers.
- Mobile marketing musts that are no longer optional, including in-app messaging, push and SMS.
More about e commerce and mobile usage:
- An estimated 10 Billion Mobile Connected Devices are currently in use
Ignoring these trends in mobile eCommerce (referred to as m-Commerce in the industry) evolution means potentially missing out on more and more profit as these trends continue. Here are some tips to make your website mobile friendly:
- Your website should be programmed to intuitively adapt to whatever device is accessing it in order to provide the most user-friendly experience
- Tap-Friendly: make sure all buttons, links and calls to action have the appropriate size and margin to prevent errors.
- Text Phone Numbers: Make sure all phone numbers are text and not images so users can tap-to-call, or copy and paste the number to share with a friend.
- Visual Content: Since mobile websites are usually viewed on the go and on much smaller screens, utilizing visual content such as infographics and videos will be preferred over reading lengthy text.
- Main Navigation: increase padding around menu items so it’s easy for the user to read and tap on menu items.
- Contact Forms: Increase form input fields so it’s easy for the user to fill out the form.
Think of the above statement 10 billion!!!! You must be mobile or mobile ready on your web site!
More:
eCommerce Mobile Stats
- 125 Million U.S. consumers own smartphones
- 50 million U.S. Consumers own tablets
- 62% of smartphone users have made a purchase online using their mobile device in the last 6 months
- One third of all ecommerce purchases during the 2015 holiday season were made on a smartphone.
- eCommerce dollars now comprise 10% of ALL retail revenue
- 80% of shoppers used a mobile phone inside of a physical store to either look up product reviews, compare prices or find alternative store locations
- An estimated 10 Billion Mobile Connected Devices are currently in use
Some of the above info came from emarsys and from Outerbox.
More to come! We make mobile web sites, we make mobile phone application.
Talk soon
Joe Rossini
Thursday, August 31, 2017
The new ad war is coming!
A new on line ad war is brewing and the good thing is it will give us all more abilities to market products. here is a hint:
As an early sales exec at Google, Tim Armstrong was well paid, but itchy for a bigger challenge, so he left to run AOL. Now, as the chief of both AOL and Yahoo under Verizon, he has the challenge of a lifetime: Making an ad business work when Google and Facebook are taking all the ad dollars.
“I think the worst thing we could do is — Facebook and Google are Olympic athletes with gold medal performances,” Armstrong said on the latest episode of Recode Media with Peter Kafka. “We have a differentiated strategy to partner with Google and Facebook, but not directly compete with them.”
Instead, AOL and Yahoo — which are collectively known as Oath — will find ways to give advertisers things the big steamrollers can’t. But Armstrong isn’t revealing much about his unique solutions, yet.
“I’m not going to go deeply into our strategy, but we have a different distribution model, different measurement model and different data model than they’re building,” Armstrong said. “I think you will see us, over the course of the next 12 months, roll out a series of products that are differentiated from Google and Facebook.”
“This is also not a winner-take-all market,” he added. “As big as those guys are, and they are big and they are ferocious from a competitive standpoint, there is so much opportunity left in the world.”
You can listen to the new podcast on Apple Podcasts, Spotify, Pocket Casts, Overcast or wherever you listen to podcasts.
Some new things happening:
At a technology event in June, Amazon exec David Limp said he hoped there would be a day when the company’s virtual assistant, Alexa, worked with competing digital assistants like Cortana.
Turns out he knew that that day was coming.
Amazon and Microsoft announced on Wednesday that they’ve been working on a partnership to allow their respective voice assistants, Alexa and Cortana, to speak to one another.
Starting later this year, owners of Amazon Echos and other Alexa-powered devices will be able to say: “Alexa, open Cortana” to start querying Microsoft’s voice assistant. Owners of devices running Microsoft’s Windows 10 operating system will be able to summon Alexa via Cortana in a similar manner.
Cyber security:
In 2012, the New York Times’s David Sanger broke a bombshell story detailing a joint US-Israel cyber attack on Iran that undermined its nuclear enrichment facilities. The computer virus, dubbed “Stuxnet,” disabled 1,000 of Iran’s 5,000 centrifuges at the time.
In 2014, a Chinese hacking group, known as Unit 61398, penetrated the computer networks of major US companies like Westinghouse and US Steel in order to loot trade secrets. This was one of numerous such attacks by Unit 61398.
In 2016, Russian government hackers gained access to Democratic National Committee computer networks, stole sensitive information, and systematically leaked it in an effort to damage Hillary Clinton’s presidential campaign.
And just a week ago, the Washington Post reported that the United Arab Emirates had hacked various Qatari government social media accounts, sparking one of the most dangerous diplomatic crises in the Middle East in decades.
A new book, The Darkening Web, argues that stories like these are going to become more and more common as countries seek to project power in cyberspace. The author is Alexander Klimburg, a program director at the Hague Centre for Strategic Studies and an adviser to several governments and international organizations on cybersecurity strategy and internet governance.
Klimburg games out a few possible futures for the internet. One of them is apocalyptic: Imagine the world’s major powers unleashing malicious code on one another, irreparably destroying vital infrastructure. Another is an Orwellian world in which the internet has become a tool of subjugation, monitored and restricted by state powers. Still another possibility is that the internet remains free, controlled by non-state actors, and a wondrous instrument of global connection.
It’s hard to say which of these scenarios is most likely. For Klimburg, it’s a matter of mobilizing concern now before it’s too late. “Ultimately,” he told me, “it will take the attention of the free society that built the internet to save it.”
More to come soon!
Joe Rossini
Monday, August 28, 2017
What is happening in retail e commerce
In case you missed it: On the heels of Walmart
announcing a partnership with Google that will allow shoppers to order
products through Google Assistant, Walmart head of e-commerce Marc Lore will discuss the company's approach to innovation at Shop.org, to be held Sept. 25-27 in Los Angeles.
Retail is not dead! There are more than 1 million retail establishments across the US, and retail sales have been growing at almost 4% annually since 2010. Source: Census Bureau and NRF via NRF on Instagram.
Target has completed a $10 million makeover of its downtown Minneapolis store, and the new look reflects the retailer's focus on the shopping experience in the digital age. Specialty lighting replaces fluorescent bulbs, beacons let shoppers open in-app maps to navigate the store, and the grocery department sports a new upgraded design ( Look at the use of in store apps).
Casey's General Store is set to build new stores, increase acquisitions, expand its digital platform, improve price optimization and cut back on expenses, according to Wells Fargo Securities' Bonnie Herzog. The retailer is hoping to increase its footprint in small communities in new and existing markets, especially in Illinois and Wisconsin, Herzog said. (Again look at the potential use digital platform)
Amazon will take control of Whole Foods Market on Monday with a plan to immediately cut prices on a slew of organic items and ultimately meld in-store and online retail. The e-commerce giant will sell Whole Foods' private labels online and install Amazon lockers for the pickup and return of online orders in some stores.
The bottom line is that retail and business is continuing to move to e commerce and making their brick and mortar link even closer to the web! Review your SEO and e-commerce if you use it to sell more! We can help you, call us.
Joe Rossini
Retail is not dead! There are more than 1 million retail establishments across the US, and retail sales have been growing at almost 4% annually since 2010. Source: Census Bureau and NRF via NRF on Instagram.
Target has completed a $10 million makeover of its downtown Minneapolis store, and the new look reflects the retailer's focus on the shopping experience in the digital age. Specialty lighting replaces fluorescent bulbs, beacons let shoppers open in-app maps to navigate the store, and the grocery department sports a new upgraded design ( Look at the use of in store apps).
Casey's General Store is set to build new stores, increase acquisitions, expand its digital platform, improve price optimization and cut back on expenses, according to Wells Fargo Securities' Bonnie Herzog. The retailer is hoping to increase its footprint in small communities in new and existing markets, especially in Illinois and Wisconsin, Herzog said. (Again look at the potential use digital platform)
Amazon will take control of Whole Foods Market on Monday with a plan to immediately cut prices on a slew of organic items and ultimately meld in-store and online retail. The e-commerce giant will sell Whole Foods' private labels online and install Amazon lockers for the pickup and return of online orders in some stores.
The bottom line is that retail and business is continuing to move to e commerce and making their brick and mortar link even closer to the web! Review your SEO and e-commerce if you use it to sell more! We can help you, call us.
Joe Rossini
Friday, August 25, 2017
A little this and a little that..........
From Google:
Bad landing pages, especially on mobile devices, can kill conversions. There are high bounce rates if users can’t find desired information or the user experience is too cumbersome or slow.
To help advertisers improve mobile performance, Google announced a new Landing Pages tool at Google Marketing Next earlier this year. It’s designed to help marketers assess the mobile-friendliness of various URLs on their sites (as opposed to their entire sites). It is being rolled out in the next few weeks as a tab in the new AdWords experience.
Determining a marketing budget can be frustrating. Are you investing enough? Are your marketing dollars being applied in the most efficient way? How do you know if what you’re doing is working?
At Rossini.com we do not just pick one way to market we use multiple ways such as social media, blogging, submits to the search engines, PR releases and much more. I believe as the saying use to be "it takes a village" the more the better!
Do keywords really matter anymore? I say yes they do and at the very least it gets you thinking of what you do and how people should search for you. Short keywords are not good but longer more specific ones are. Make sure you have keywords in your programming.
From Facebook...
Facebook is curtailing the types of organic posts that Pages can convert into ads as it looks to make the purpose of its ads more precise, the company announced on Thursday.
Up until now, brands have been able to take any post published to their Pages and amplify its reach by paying Facebook to run it as an ad in people’s news feeds. That won’t be the case for much longer as Facebook continues to orient its ad product around delivering actual business results, as opposed to simple social engagement, which was something that COO Sheryl Sandberg emphasized repeatedly during the company’s most recent earnings call.
“We want businesses to utilize Facebook ad products that give them the best opportunity to achieve their business goals, and removing these inessential boosting options will reduce complexity and help them find the right products to get the best results,” said Facebook product manager Jyotika Prasad in an emailed statement.
Under what works....l
The popular narrative around the rise of the mobile web and smartphone apps has been one of increasing audience fragmentation. But the opposite may actually be happening — concentration and consolidation.
More digital media time is concentrated in smartphone apps than on the mobile web or PC. And most of that time is spent in a small number of apps, led by Facebook. Users are also downloading fewer new apps, so it’s getting harder to break through. Earlier today, comScore published its 2017 US Mobile App Report detailing these trends.
Digital media time spent with the desktop stands at 34 percent, with smartphone apps at 50 percent. Tablet and mobile web represent the remaining 16 percent. And though it sees dramatically lower engagement, the mobile web has roughly 2x the reach of mobile apps.
OK some of these tidbits comes from me and from Search Engine Land
Talk soon
Joe Rossini
Bad landing pages, especially on mobile devices, can kill conversions. There are high bounce rates if users can’t find desired information or the user experience is too cumbersome or slow.
To help advertisers improve mobile performance, Google announced a new Landing Pages tool at Google Marketing Next earlier this year. It’s designed to help marketers assess the mobile-friendliness of various URLs on their sites (as opposed to their entire sites). It is being rolled out in the next few weeks as a tab in the new AdWords experience.
Determining a marketing budget can be frustrating. Are you investing enough? Are your marketing dollars being applied in the most efficient way? How do you know if what you’re doing is working?
At Rossini.com we do not just pick one way to market we use multiple ways such as social media, blogging, submits to the search engines, PR releases and much more. I believe as the saying use to be "it takes a village" the more the better!
Do keywords really matter anymore? I say yes they do and at the very least it gets you thinking of what you do and how people should search for you. Short keywords are not good but longer more specific ones are. Make sure you have keywords in your programming.
From Facebook...
Facebook is curtailing the types of organic posts that Pages can convert into ads as it looks to make the purpose of its ads more precise, the company announced on Thursday.
Up until now, brands have been able to take any post published to their Pages and amplify its reach by paying Facebook to run it as an ad in people’s news feeds. That won’t be the case for much longer as Facebook continues to orient its ad product around delivering actual business results, as opposed to simple social engagement, which was something that COO Sheryl Sandberg emphasized repeatedly during the company’s most recent earnings call.
“We want businesses to utilize Facebook ad products that give them the best opportunity to achieve their business goals, and removing these inessential boosting options will reduce complexity and help them find the right products to get the best results,” said Facebook product manager Jyotika Prasad in an emailed statement.
Under what works....l
The popular narrative around the rise of the mobile web and smartphone apps has been one of increasing audience fragmentation. But the opposite may actually be happening — concentration and consolidation.
More digital media time is concentrated in smartphone apps than on the mobile web or PC. And most of that time is spent in a small number of apps, led by Facebook. Users are also downloading fewer new apps, so it’s getting harder to break through. Earlier today, comScore published its 2017 US Mobile App Report detailing these trends.
Digital media time spent with the desktop stands at 34 percent, with smartphone apps at 50 percent. Tablet and mobile web represent the remaining 16 percent. And though it sees dramatically lower engagement, the mobile web has roughly 2x the reach of mobile apps.
OK some of these tidbits comes from me and from Search Engine Land
Talk soon
Joe Rossini
Monday, August 14, 2017
Fake News, Terrorist propaganda! Google is moving to fight this!
Google is preparing to release new filters which would give advertisers greater control over the content they appear against.
According to the Times – which ran a front-page exposé earlier this year into how advertisers like M&S were appearing next to extremist content – Google is planning to grade videos and other online content under new parameters which include violence, nudity and political satire.
Offering an example, the Times said it “would hand advertisers the power to block their adverts appearing alongside a bawdy comedy sketch, for example, or risqué music video.”.
The additional safeguards are expected to come into force by the end of the year.
It comes after Google revealed that it would invest heavily in artificial intelligence in an effort to better identify extremist and terrorism-related content, specifically on YouTube.
YouTube claimed that during the past month of testing AI-powered detection and removal tools that over 75% of the videos it has removed for violent extremism were purged before receiving a single human flag. The platform has said it believes the accuracy of its systems have improved “dramatically” due to machine learning.
It’s part of an a four-pronged strategy to appease the industry after major advertisers, in wake of the Times investigation, pulled ad spend from YouTube and the Google Display Network.
This article is about: World, Google, Youtube, Brand Safety, Digital, BrandAccording to the Times – which ran a front-page exposé earlier this year into how advertisers like M&S were appearing next to extremist content – Google is planning to grade videos and other online content under new parameters which include violence, nudity and political satire.
Offering an example, the Times said it “would hand advertisers the power to block their adverts appearing alongside a bawdy comedy sketch, for example, or risqué music video.”.
The additional safeguards are expected to come into force by the end of the year.
It comes after Google revealed that it would invest heavily in artificial intelligence in an effort to better identify extremist and terrorism-related content, specifically on YouTube.
YouTube claimed that during the past month of testing AI-powered detection and removal tools that over 75% of the videos it has removed for violent extremism were purged before receiving a single human flag. The platform has said it believes the accuracy of its systems have improved “dramatically” due to machine learning.
It’s part of an a four-pronged strategy to appease the industry after major advertisers, in wake of the Times investigation, pulled ad spend from YouTube and the Google Display Network.
This article from Google and By Jennifer Faull
I believe we must fight this on Facebook and other modes of social media. I believe our last election was interfered with on both sides and this needs to change and perhaps this is a nice first step.
Joe Rossini
Friday, August 11, 2017
It has been a while
Sorry I have not written in a while, I have been very busy. I guess I have learned the hard way again that working hard is not as good as working smart. I have made tons of calls and put out lots of quotes only to get rejected because the people I am quoting to have no intention of buying or spending the incredibly small amount of money for my products they want evwen cheaper. I guess the moral to the story is dont spend time if there is really no reason to spend time. If someone says they dont have enough money or they have been taken before and the owner really is afraid of being taken again either sell harder as to why you should move forward or just say thank you, give them yur information and move on. I am ready to take this philosphy now. Bottom line is most people want everything but they cant afford ther big car or huge house so you downsize a bit. I can downsize my products but at what price? I am just going to ask up front do yu you have $1200 to $5000 for a great fancy shiny web site and if they hesiotate enough I thank them and move on. So I move on.
Monday, July 24, 2017
Is your network at risk
Is Your Site or Network at Risk?
"Web security" is relative and has two components, one internal and one public. Your relative security is high if you have few network resources of financial value, your company and site aren't controversial in any way, your network is set up with tight permissions, your web server is patched up to date with all settings done correctly, your applications on the web server are all patched and updated, and your web site code is done to high standards.
Your web security is relatively lower if your company has financial assets like credit card or identity information, if your web site content is controversial, your servers, applications and site code are complex or old and are maintained by an underfunded or outsourced IT department. All IT departments are budget challenged and tight staffing often creates deferred maintenance issues that play into the hands of any who want to challenge your web security.
If you have assets of importance or if anything about your site puts you in the public spotlight then your web security will be tested. We hope that the information provided here will prevent you and your company from being embarrassed - or worse.
It's well known that poorly written software creates security issues. The number of bugs that could create web security issues is directly proportional to the size and complexity of your web applications and web server. Basically, all complex programs either have bugs or at the very, least weaknesses. On top of that, web servers are inherently complex programs. Web sites are themselves complex and intentionally invite ever greater interaction with the public. And so the opportunities for security holes are many and growing.
Technically, the very same programming that increases the value of a web site, namely interaction with visitors, also allows scripts or SQL commands to be executed on your web and database servers in response to visitor requests. Any web-based form or script installed at your site may have weaknesses or outright bugs and every such issue presents a web security risk.
Contrary to common knowledge the balance between allowing web site visitors some access to your corporate resources through a web site and keeping unwanted visitors out of your network is a delicate one. There is no one setting, no single switch to throw that sets the security hurdle at the proper level. There are dozens of settings if not hundreds in a web server alone, and then each service, application and open port on the server adds another layer of settings. And then the web site code... you get the picture.
Add to that the different permissions you will want to grant visitors, prospects, customers, partners and employees. The number of variables regarding web security rapidly escalates.
A web security issue is faced by site visitors as well. A common web site attack involves the silent and concealed installation of code that will exploit the browsers of visitors. Your site is not the end target at all in these attacks. There are, at this time, many thousands of web sites out there that have been compromised. The owners have no idea that anything has been added to their sites and that their visitors are at risk. In the meantime visitors are being subject to attack and successful attacks are installing nasty code onto the visitor's computers.
This post compliments of Beyond Security
More to come soon.
Joe
Wednesday, July 19, 2017
How can you help a customer with their business
I am often asked how I can help a customer make more sales or improve efficiency. As a web sales specialist with marketing in mind it is one of the first things I look at about a business and that is what does the web page tell me about that business. The web site today is like the yellow pages ads of yesteryear or the newspaper ads about a company. Your ad calls out in many cases to the potential customer to call. I know I often as statistics show that the big ads get your attention and draw your eye towards it. Web pages today are similar, a very well done, neat yet professional ad with nice graphics. The web site is your opening to the world and with search engines to do the work the old phrase let your fingers do the walking is true, you type what you want and up comes returns from all over the world. As a web marketeer, I look at ways to make sure that the web site meets the criteria of what the main search engines want. Make the web site fast, make it visually nice, make it interesting. Make sure internally the correct SEO programming is in place such as key words, descriptions, title tags and more. Now once the web site is done, now you have to market it correctly. The web site can be used in many ways that I will get into soon to capture leads, and to allow your customers to get important facts. I have customers that have facts about heating and cooling systems. I have customers with facts about animals. Do you want to know about electrical systems, I have customers that have facts about that. How about putting white papers about your products on line to help your customers solve problems. The web site can be your way to keep in toch with your customers and to help them.
Ok enough for this small section, more soon.
Talk soon.
Joe
Ok enough for this small section, more soon.
Talk soon.
Joe
Subscribe to:
Posts (Atom)